Crypto Key Generate Rsa Example
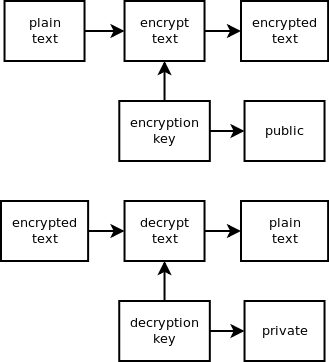
HI My goal - crypto key generated by startup config - 'no shut' a specifc interface - save the config to nvram My Script! Kron occurrence cryptokey in 2 oneshot policy-list cryptokey! Kron policy-list cryptokey cli event manager run cryptokey! Event manager applet cryptokey event none sy. Jan 14, 2018 Router(config)# crypto key generate rsa general-keys The name for the keys will be: myrouter.example.com Choose the size of the key modulus in the range of 360 to 2048 for your General Purpose Keys. Choosing a key modulus greater than 512 may take a few minutes. I'm currently experimenting with the Windows Cryptography API and running into some problems with Public-Key-Cryptography. I can find lots of examples of how to encrypt items, but nothing directly. How to generate and use public key cryptography in WinCrypt. Ask Question. Use RSA private key to generate public key? Sep 21, 2018 The Web crypto api RSA-OAEP algorithm identifier is used to perform encryption and decryption ordering to the RSAES-OAEP algorithm, using the SHA hash functions defined in this specification and using the mask generation function MGF1. This is the web cryptography api example of performing rsa oaep encryption decryption. The module Crypto.PublicKey.RSA provides facilities for generating new RSA keys, reconstructing them from known components, exporting them, and importing them. As an example, this is how you generate a new RSA key pair, save it in a file called mykey.pem, and then read it back. There are very many encryption algorithms but I am describing the Rivest, Shamir, Adleman (RSA) Algorithm. The flowcharts above shows how to generate a public and private key using RSA. Example of RSA: Here is an example of RSA encryption and decryption with generation of the public and private key. Generate public.
Encrypt data with AES¶
The following code generates a new AES128 key and encrypts a piece of data into a file.We use the EAX mode because it allows the receiver to detect anyunauthorized modification (similarly, we could have used other authenticatedencryption modes like GCM, CCM or SIV).
At the other end, the receiver can securely load the piece of data back (if they know the key!).Note that the code generates a ValueError exception when tampering is detected.
Generate an RSA key¶
The following code generates a new RSA key pair (secret) and saves it into a file, protected by a password.We use the scrypt key derivation function to thwart dictionary attacks.At the end, the code prints our the RSA public key in ASCII/PEM format:
The following code reads the private RSA key back in, and then prints again the public key:
Generate public key and private key¶
The following code generates public key stored in receiver.pem and private key stored in private.pem. These files will be used in the examples below. Every time, it generates different public key and private key pair.
Encrypt data with RSA¶
Crypto Key Generate Rsa Encryption
The following code encrypts a piece of data for a receiver we have the RSA public key of.The RSA public key is stored in a file called receiver.pem.
Since we want to be able to encrypt an arbitrary amount of data, we use a hybrid encryption scheme.We use RSA with PKCS#1 OAEP for asymmetric encryption of an AES session key.The session key can then be used to encrypt all the actual data.
Crypto Key Generate Rsa Command
As in the first example, we use the EAX mode to allow detection of unauthorized modifications.
Crypto Key Generate Rsa Command
The receiver has the private RSA key. They will use it to decrypt the session keyfirst, and with that the rest of the file: